DKIM and Encryption: Do You Really Need It?

What is DKIM and is it something you need to use along with encryption? This will help you decide!
Serving as a secure digital seal, DomainKeys Identified Mail, more commonly known by its acronym ‘DKIM,’ is a way of signing messages to help an organization’s mail server verify that the email it is receiving was not faked or altered.
How does DKIM work?
Working in tandem with Sender Policy Framework (SPF) and Domain-based Message Authentication (DMARC), DKIM is published in your domain’s DNS record so that the receiving mail server can check whether a message is trustworthy. While the SPF component tells which servers are allowed to send mail for the domain, DKIM specifically tells whether the email has been altered by verifying the domain’s secret signing key. DMARC instructs further actions based on the results of SPF and DKIM, like whether to reject a seemingly compromised message.
DKIM makes “phishing” much harder
Together, SPF, DKIM and DMARC create a digital signing process that helps assure a message’s origin and content. Simply put, it makes phishing much harder by stopping spammers from using an organization’s email address to send forged email pretending to be from them.
Do we need DKIM to be used along with Echoworx?
DKIM is used to detect spoofing of the sender’s domain. This provides protection from message modification, identify theft, and repudiation. DKIM does not provide email and attachment encryption.
As part of our commitment to protecting the information you share, Echoworx offers DKIM support in addition to email encryption.
Echoworx can apply DKIM signatures to encrypted messages we send on an organization’s behalf. Instances where DKIM services are applicable include messages sent directly from the Echoworx Email Encryption gateway, like with TLS delivery, or when an organization does not have, but requires, access to DKIM capabilities. Under these circumstances, a message is routed to Echoworx prior to delivery, DKIM signatures and encryption are applied, and the message is sent on the sender’s behalf by Echoworx.
While broken or incomplete signatures are specified as missing signatures under original DKIM rules, this is not how they have played out in practice. Most services treat broken or incomplete DKIM signatures as faulty and, in turn, as spam, which hurts your reputation as a sender. To help address this issue, and improve deliverability, Echoworx Email Encryption can be configured to strip off existing DKIM signatures to prevent broken or compromised signatures before sending.
Turning ‘on’ DKIM with Echoworx
Activating or integrating DKIM with an existing email infrastructure should be a simple and painless process. With Echoworx, DKIM can be turned on or off at the click of a button for messages sent from the gateway or portal. With three settings for DKIM, Echoworx allows organizations to configure headers to scope for DKIM, strip DKIM signatures or add DKIM signature headers for outgoing messages to domains which support them.
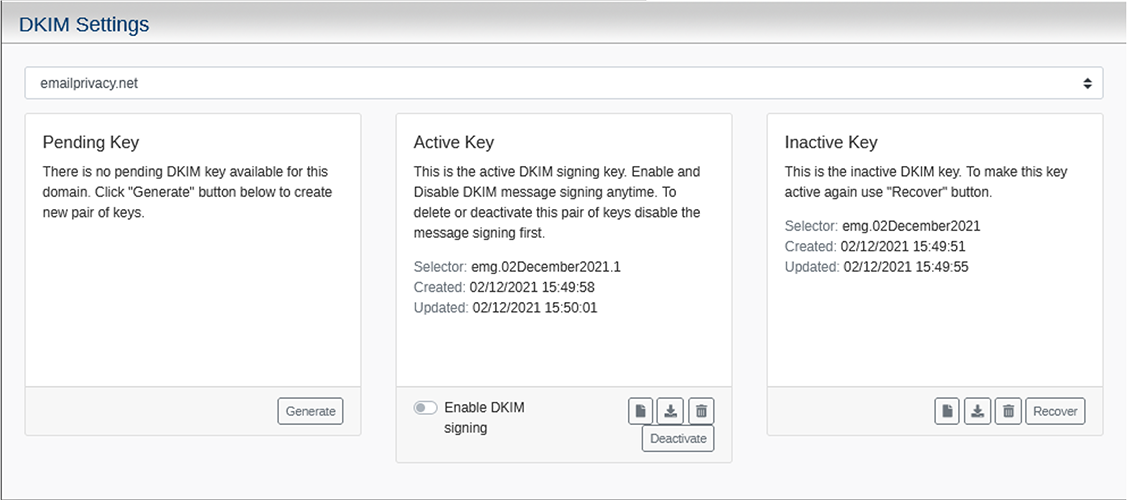
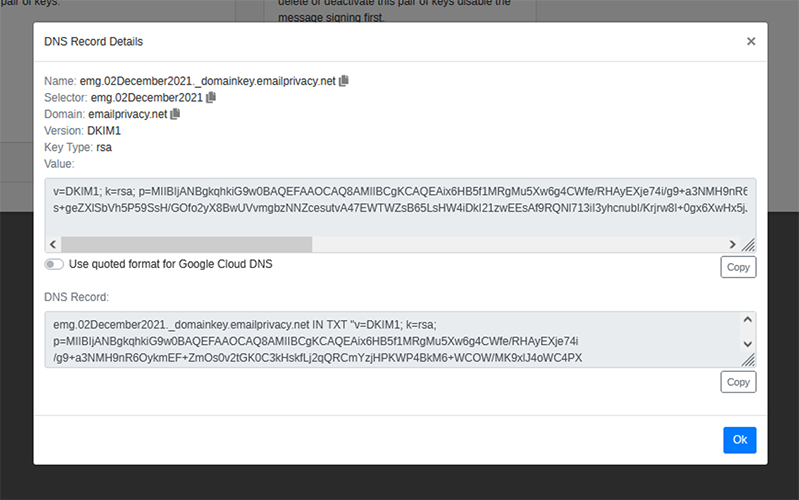
Public keys, used for DKIM signatures, can be easily generated within the Echoworx platform. These keys can be used for organizations who demand them. All DKIM keys may be created, managed or deleted directly in the platform without any complicated steps. Entire DNS entries may be exported as a text file which may then be uploaded into a designated DNS zone or may be copied and pasted directly into a domain management console.
If you would like to learn more about the sending capabilities of the platform or see a personalized demonstration, please reach out to book a demo with one of our encryption experts.
