Email Data Protection, The What and Why, and How to Select Yours

Organizations continue to place too much focus on feature and function when evaluating security technology – and not enough on value or long-term implementation.
At a time of fierce digital transformation, the distance between technical promise and business impact continues to widen as over 124.5 billion business emails are sent and received each day.
When COVID-19 first emerged, many organizations scrambled to find quick-fix security solutions to prop up their now-remote workforces for a business delay expected to last a couple of weeks. Add to the mix the acceleration of long-term working from home and shifting attitudes to digital privacy.
“This is a wake-up call for organizations that have placed too much focus on daily operational needs at the expense of investing in digital business and long-term resilience,” says Sandy Shen, Senior Director Analyst at Gartner. “Businesses that can shift technology capacity and investments to digital platforms will mitigate the impact of the outbreak and keep their companies running smoothly now, and over the long term.”
But simply buying an encryption product, to protect your data being sent in email, does not guarantee long term organizational value.
According to a survey from email encryption technology experts Echoworx, 81 per cent of organizations prioritized encryption for protecting data sent in email as important, even critical, to their technology stack, but only 40 per cent are using email encryption throughout their business.
To end this disconnect, we argue that organizations need to start thinking differently about their email data protection strategy and the way they evaluate and select solutions and vendors.
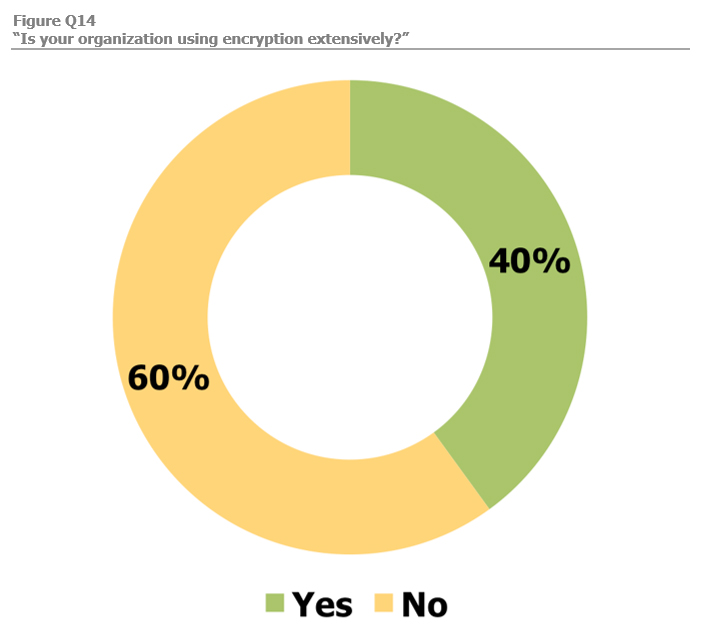
Despite the importance of encryption and the benefits that it offers, only two in five organizations report that encryption is used extensively – Echoworx Encryption & Authentication Survey
Technology alone delivers no value
Despite technical “experts” believing a technology or product will work for the business is no guarantee that the business will actually use it. Through our years of experience providing email encryption solutions, we have heard three misconceptions repeated over and over.
Misconception #1: “We invest in encryption tools because it is mandatory”
Reality: Investment in an encryption tool should address specific business needs.
Misconception #2: “We have encryption, we are safe. It’s good enough.”
Reality: Protecting data sent through email is less dependent on technology than you think.
Misconception #3: “Data protection is all about compliance”
Reality: The ability to protect data is just as important as the ability to use and move data.
Why do you need a particular product? How well do you know the business and their needs? And, how well will this product meet those needs? If you don’t know the answer to these questions, with total clarity, you don’t understand the business and you won’t be able to add real value.
One bank, for example, wanted to easily recall emails and customer documentation so that they could reduce implicating the Chief Data Officer and eliminate lengthy audit processes. That’s what the business needed. What the business got was an onerous multi-step approach, requiring physical actions from multiple staff, external individuals, organizations, and 3rd party email providers to confirm emails and attachments have been deleted from all backups and archives.
In another example, an insurance company wanted their customers to be able to simply respond to an email so that they could return sensitive documentation easily to a centralized mailbox. That’s what the business wanted. What the business got was a time-consuming multi-step approach, requiring the resources of multiple staff, sending instructional emails to customers, requiring registration to an encrypted email service – before being able to access and return requested documents safely.
The list goes on.
Ask better questions, align technology to business needs
Instead of arming yourself with a checklist of features and functions, prepare questions that will help you evaluate the fit of an email data encryption solution to your business needs. How well does this offering resolve your specific need, does it fit into your existing way of working and can it meet your bigger picture needs tomorrow?
